Introduction
In today’s rapidly evolving digital landscape, businesses and organizations are continuously facing sophisticated cyber threats that can cause significant financial, operational, and reputational damage. As cybercriminals become increasingly adept at exploiting vulnerabilities, companies need a proactive approach to security-enter threat intelligence. By leveraging threat intelligence, organizations gain deep insights into the tactics, techniques, and procedures used by cyber adversaries, empowering them to predict, prevent, and mitigate potential attacks.
Definition
Threat intelligence is information about possible or current cyber threats that is gathered, analyzed, and shared. It entails obtaining and evaluating data regarding malware, ransomware, phishing, and advanced persistent threats (APTs), among other threat categories, in order to comprehend the strategies, methods, and processes (TTPs) employed by cybercriminals.
Understanding Threat Intelligence
Threat intelligence is the process of collecting, analyzing, and applying information about potential or active cyber threats. This information is gathered from a wide range of sources, including open-source data, internal telemetry, industry reports, and even dark web forums. The ultimate goal is to transform raw data into actionable insights that enable organizations to bolster their security posture.
At its core, threat intelligence is divided into three primary categories:
- Strategic Threat Intelligence: This type provides high-level insights into the broader threat landscape, including trends, motivations, and geopolitical factors influencing cyber attacks. It is primarily aimed at executives and decision-makers.
- Tactical Threat Intelligence: This involves the details of the attack methodologies, including indicators of compromise (IOCs), malware signatures, and attack vectors. Tactical intelligence is invaluable for the technical teams responsible for configuring and tuning security defenses.
- Operational Threat Intelligence: This focuses on real-time details about ongoing attacks and adversary behavior. It helps organizations to react promptly by providing context-specific information that can be directly applied to incident response efforts.
The Role of Threat Intelligence in Cyber Attack Prevention
Threat intelligence serves as a critical component in modern cybersecurity strategies. Here are several ways it helps prevent cyber attacks:
Proactive Risk Management:
By continuously monitoring and analyzing threat data, organizations can identify emerging risks before they become full-blown incidents. This proactive stance allows security teams to patch vulnerabilities, adjust firewall rules, and update intrusion detection systems based on the latest threat trends. Instead of waiting for an attack to occur, businesses can stay one step ahead by anticipating potential threats.
Enhanced Incident Response:
In the event of a cyber attack, time is of the essence. With threat intelligence, security teams have immediate access to detailed information about the nature and origin of the attack. This accelerates the incident response process by providing context that aids in quickly containing the threat and mitigating its impact. Rapid response not only minimizes damage but also reduces downtime and associated recovery costs.
Informed Decision-Making:
Executives and IT leaders are tasked with making critical decisions about resource allocation, risk management, and policy formulation. Threat intelligence provides them with the empirical data needed to justify investments in cybersecurity technologies and personnel. It also helps in aligning cybersecurity strategies with overall business objectives, ensuring that security measures are both effective and cost-efficient.
Improved Security Posture:
Regular integration of threat intelligence into security operations leads to continuous improvement in an organization’s defense mechanisms. By staying updated on the latest attack vectors and vulnerabilities, companies can implement better security controls, conduct more effective employee training, and refine their incident response plans. This iterative process ensures that the organization’s defenses evolve in tandem with the threat landscape.
Important Elements of a Successful Threat Intelligence Program
For threat intelligence to be truly effective, organizations must focus on several critical components:
Data Collection and Aggregation:
An effective threat intelligence program relies on the continuous collection of data from diverse sources. These sources might include internal logs, third-party threat feeds, and social media monitoring. Aggregating data from multiple channels provides a comprehensive view of the threat landscape and enhances the accuracy of the intelligence produced.
Data Analysis and Correlation:
Once data is collected, the next step is to analyze and correlate it to identify patterns and anomalies. Advanced analytical tools, including machine learning and artificial intelligence, are increasingly used to sift through vast amounts of data and extract meaningful insights. This process transforms raw data into actionable intelligence that can inform decision-making.
Threat Sharing and Collaboration:
Cybersecurity is not an isolated challenge; it is a collective endeavor. Many organizations participate in information sharing groups and industry consortia to exchange threat intelligence. This collaborative approach enhances the quality and scope of the intelligence available, allowing members to benefit from the collective experience of the community.
Integration with Security Tools:
To maximize its impact, threat intelligence must be seamlessly integrated with an organization’s security infrastructure. This includes firewalls, intrusion detection systems, endpoint security solutions, and security information and event management (SIEM) platforms. Automated integration ensures that threat intelligence is used in real time, enabling rapid detection and response to potential threats.
Real-World Applications of Threat Intelligence
Numerous organizations have already reaped the benefits of integrating threat intelligence into their cybersecurity strategies. Consider the following examples:
- Financial Institutions: Banks and financial services firms are prime targets for cybercriminals due to the sensitive nature of the data they hold. By leveraging threat intelligence, these institutions can detect phishing attempts, fraudulent transactions, and other malicious activities in their early stages, thereby preventing significant financial losses.
- Healthcare Providers: Hospitals and clinics manage vast amounts of patient data, making them attractive targets for ransomware attacks. Threat intelligence helps healthcare providers identify vulnerabilities and suspicious activities, ensuring that patient data remains secure and that services are not disrupted.
- Government Agencies: With the increasing threat of state-sponsored cyber attacks, government agencies rely on threat intelligence to protect critical infrastructure and sensitive national security information. Real-time intelligence allows for the rapid identification and neutralization of potential threats, safeguarding public assets.
Challenges in Implementing Threat Intelligence
While threat intelligence offers immense benefits, organizations must navigate several challenges to implement it effectively:
- Data Overload: The sheer volume of data can be overwhelming. Without proper tools and expertise, organizations risk drowning in information, which can obscure critical insights.
- False Positives: Not all alerts are indicative of genuine threats. Security teams must develop robust processes to differentiate between false positives and actual risks to avoid unnecessary disruptions.
- Resource Constraints: Implementing an effective threat intelligence program requires significant investments in technology, personnel, and training. Allocating the required resources may be difficult for smaller organizations in particular.
- Timely Integration: The fast-paced nature of cyber threats means that intelligence must be integrated and acted upon in real time. Delays in processing or applying threat intelligence can reduce its effectiveness.
Best Practices for Maximizing the Benefits of Threat Intelligence
To overcome these challenges and fully harness the power of threat intelligence, organizations should adopt several best practices:
- Establish Clear Objectives: Define what the organization aims to achieve with its threat intelligence program. This might include reducing incident response times, improving vulnerability management, or enhancing overall risk visibility.
- Invest in Automation: Utilize advanced analytics and automation tools to handle the volume of data and speed up the identification of threats. Automation can significantly reduce the burden on security teams and improve response times.
- Foster a Culture of Collaboration: Encourage collaboration both within the organization and with external partners. Sharing intelligence and best practices can lead to more comprehensive and effective security strategies.
- Continuously Update and Test: Cyber threats are constantly evolving, and so too should your threat intelligence program. Regularly update your data sources, analytical tools, and response protocols, and conduct simulations and drills to ensure preparedness.
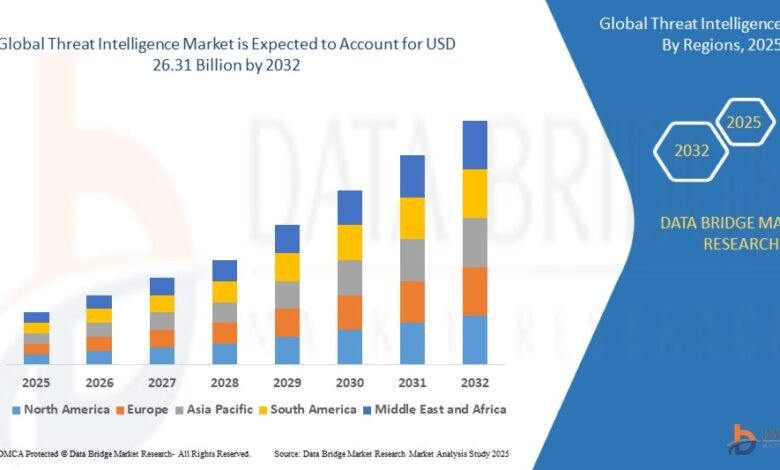
Growth Rate of Threat Intelligence Market
According to Data Bridge Market Research, the size of the worldwide threat intelligence market was estimated at USD 14.29 billion in 2024 and is expected to grow at a compound annual growth rate (CAGR) of 7.92% from 2025 to 2032, reaching USD 26.31 billion.
Conclusion
In an era where cyber attacks are not just possible but inevitable, threat intelligence stands out as a vital tool in the cybersecurity arsenal. By providing a proactive, informed, and dynamic approach to security, threat intelligence enables organizations to detect, prevent, and mitigate cyber attacks before they cause irreparable harm. As businesses continue to digitize their operations and expand their online presence, integrating threat intelligence into everyday security practices is not just advisable it is essential.




